Cloud Native OCI
Storefront + Edge
 +
+

Created with ❤ by Oracle A-Team
Table of Contents
Lab Overview
- Exposing the application
- DNS Configuration
- OKE Ingress
- Securing with WAF
Ingress
Shown here is a basic service diagram for the way traffic flows to an application deployed on OKE
 DNS
DNS
 LB
LB
 VCN
VCN
![DNS]() DNS
DNS
The Oracle Cloud Infrastructure Domain Name System (DNS) service lets you create and manage your DNS zones. You can create zones, add records to zones, and allow Oracle Cloud Infrastructure's edge network to handle your domain's DNS queries.
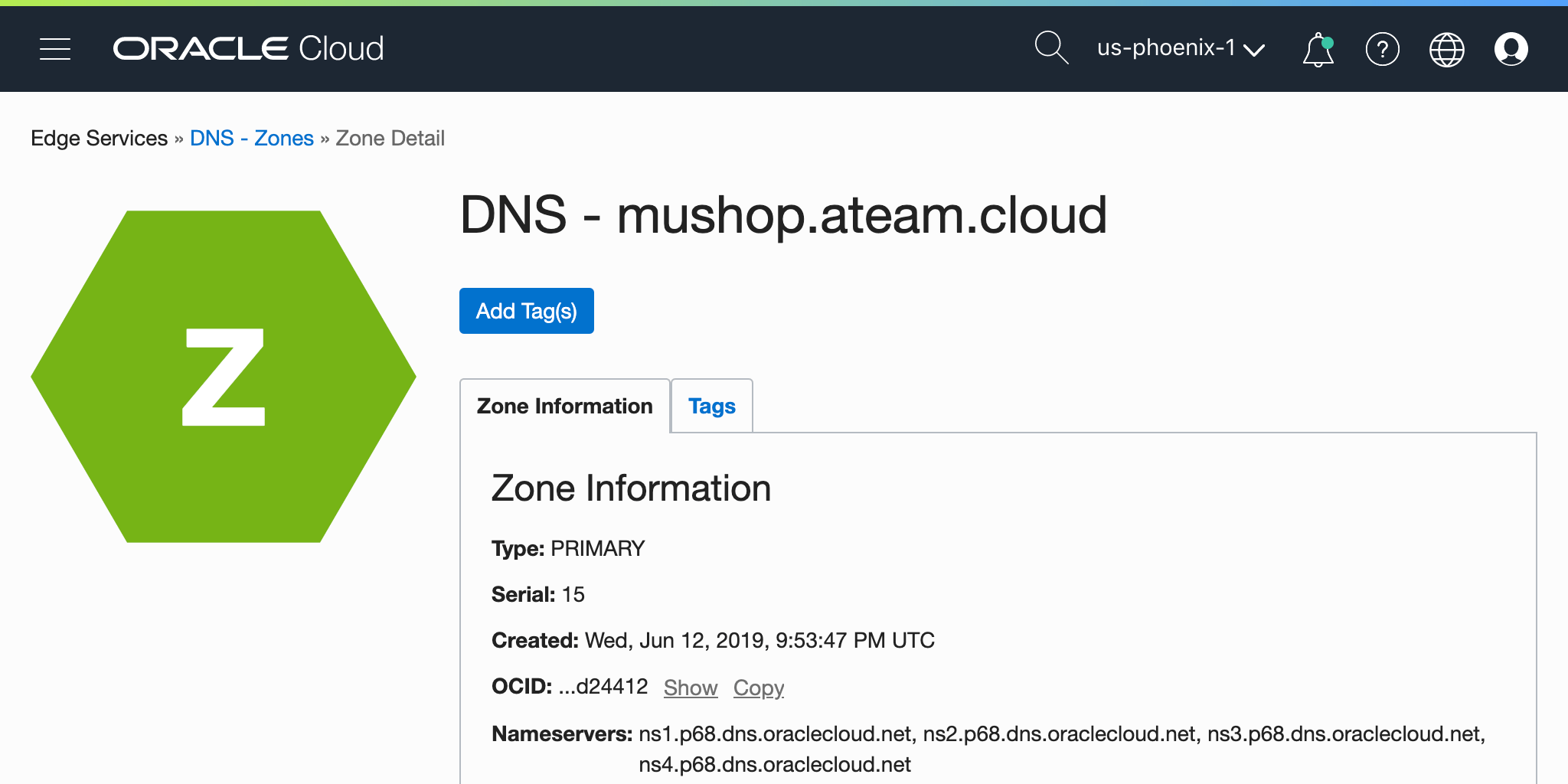
✏️ DNS Zone may also be used as part of Traffic Steering Policies
OKE Ingress

Ingress exposes HTTP and HTTPS routes from outside the cluster to services within the cluster. Traffic routing is controlled by rules on the Ingress resource
 LB
LB
 VCN
VCN
Explore how this works...
First an ingress controller is installed
helm repo add stable https://kubernetes-charts.storage.googleapis.comhelm install nginx-ingress stable/nginx-ingress \
--namespace nginx-ingresskubectl get svc -n nginx-ingressNAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
nginx-ingress-controller LoadBalancer 10.96.89.25 129.146.192.154 80:32491/TCP,443:31240/TCP 5mAn EXTERNAL-IP is assigned after a few seconds
Next verify the load balancer in OCI
oci lb load-balancer list \
--compartment-id <compartment> \
| jq '.data[] | {id: .id, name: .["display-name"], ipAddr: .["ip-addresses"][]["ip-address"]}'{
"id": "ocid1.loadbalancer.oc1.phx.aaaaaaaaucgamttt3piveonxw5d6ssirzxprcbrcv7vf6tgswna7qxdnvnfa",
"name": "097f5359-9165-11e9-bfe8-0a580aed21e9",
"ipAddr": "129.146.192.154"
}Notice 👀 ipAddr matches EXTERNAL-IP assigned to the controller 🤘
Then deploy ingress on the cluster
kubectl apply -f deploy/complete/kubernetes/ingress/mushop-dev.yamlapiVersion: extensions/v1beta1
kind: Ingress
metadata:
name: mushop-dev
annotations:
kubernetes.io/ingress.class: nginx
spec:
rules:
- http:
paths:
- path: /
backend:
serviceName: edge
servicePort: 80kubectl get ingress mushop-dev🔒 Web Application Firewall
The WAF service uses a layered approach to protect web applications against cyberattacks. This service includes over 250 predefined Open Web Access Security Project (OWASP), application, and compliance-specific rules.
- Over 250 predefined Open Web Access Security Project (OWASP), application, and compliance-specific protection rules
- Aggregated threat intelligence from multiple sources, including Webroot BrightCloud®
- Advanced Bot management with JavaScript verification, CAPTCHA challenge, whitelisting, device fingerprinting, and human interaction algorithms
- Rule-based access control including HTTP headers, URL patterns, geolocation, and IP address characteristics
- Layer 7 distributed denial-of-service (DDoS) attack protection
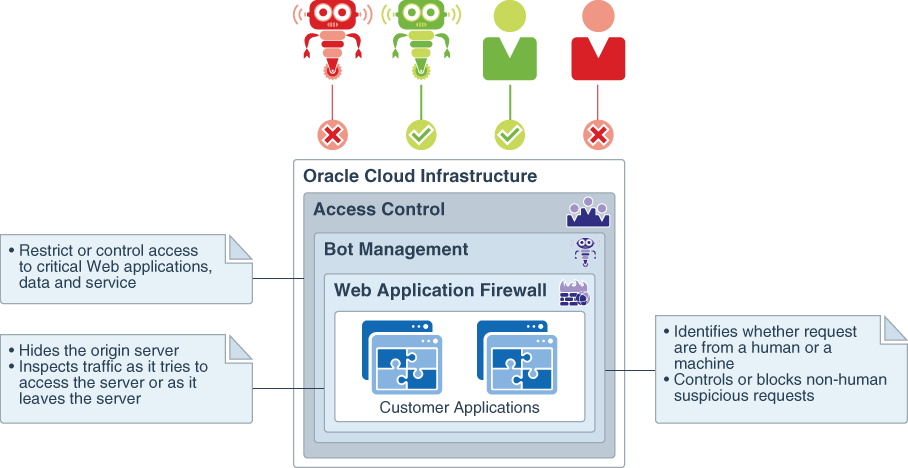
OCI Web Application Acceleration and Security Services
Ingress with WAF
WAF security added between DNS and load balance r
 DNS
DNS
 🔒 WAF
🔒 WAF
 LB
LB
 VCN
VCN
WAF in OCI Console
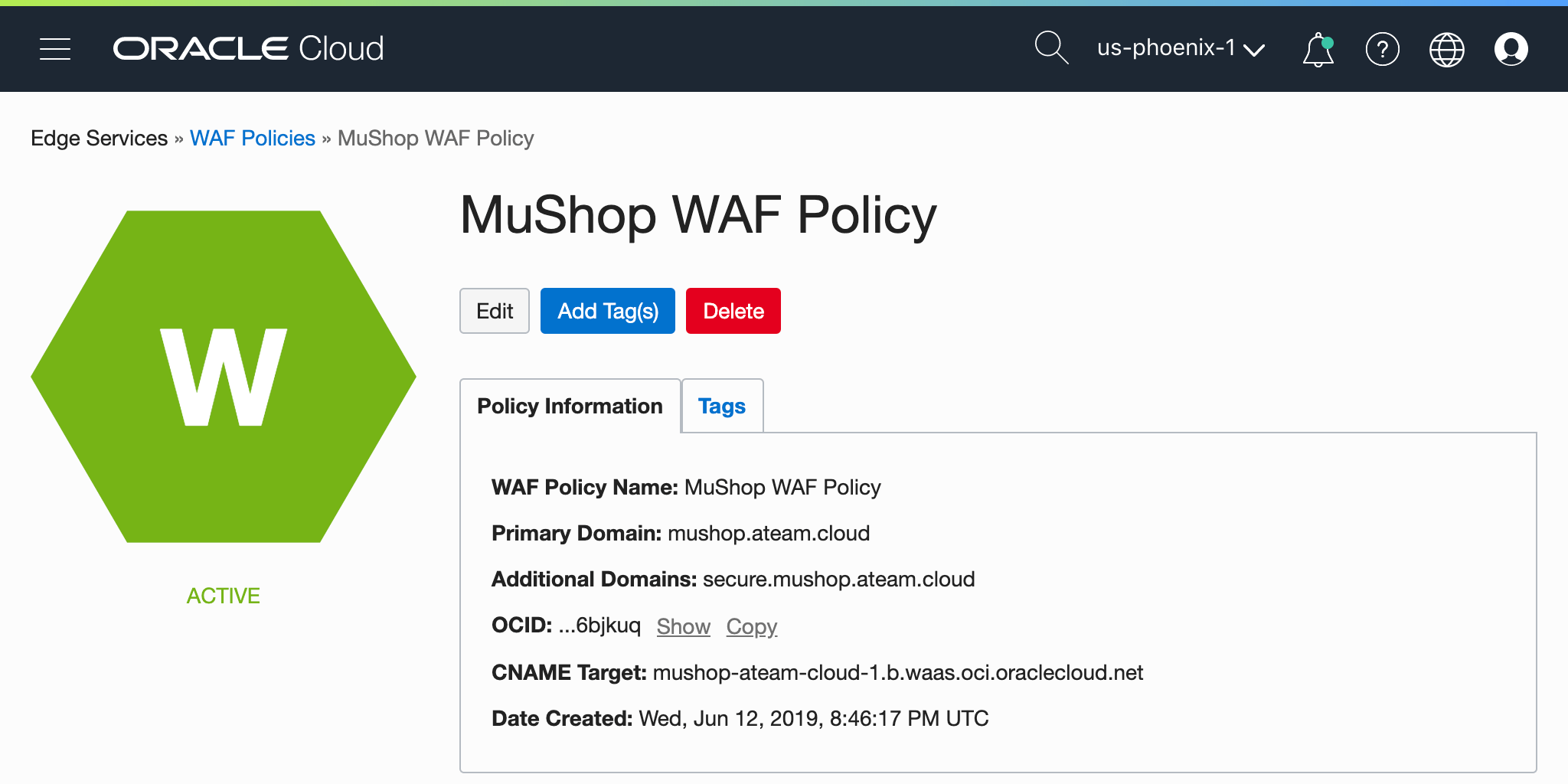
oci waas waas-policy list --compartment-id <compartment>WAF Protection Rules
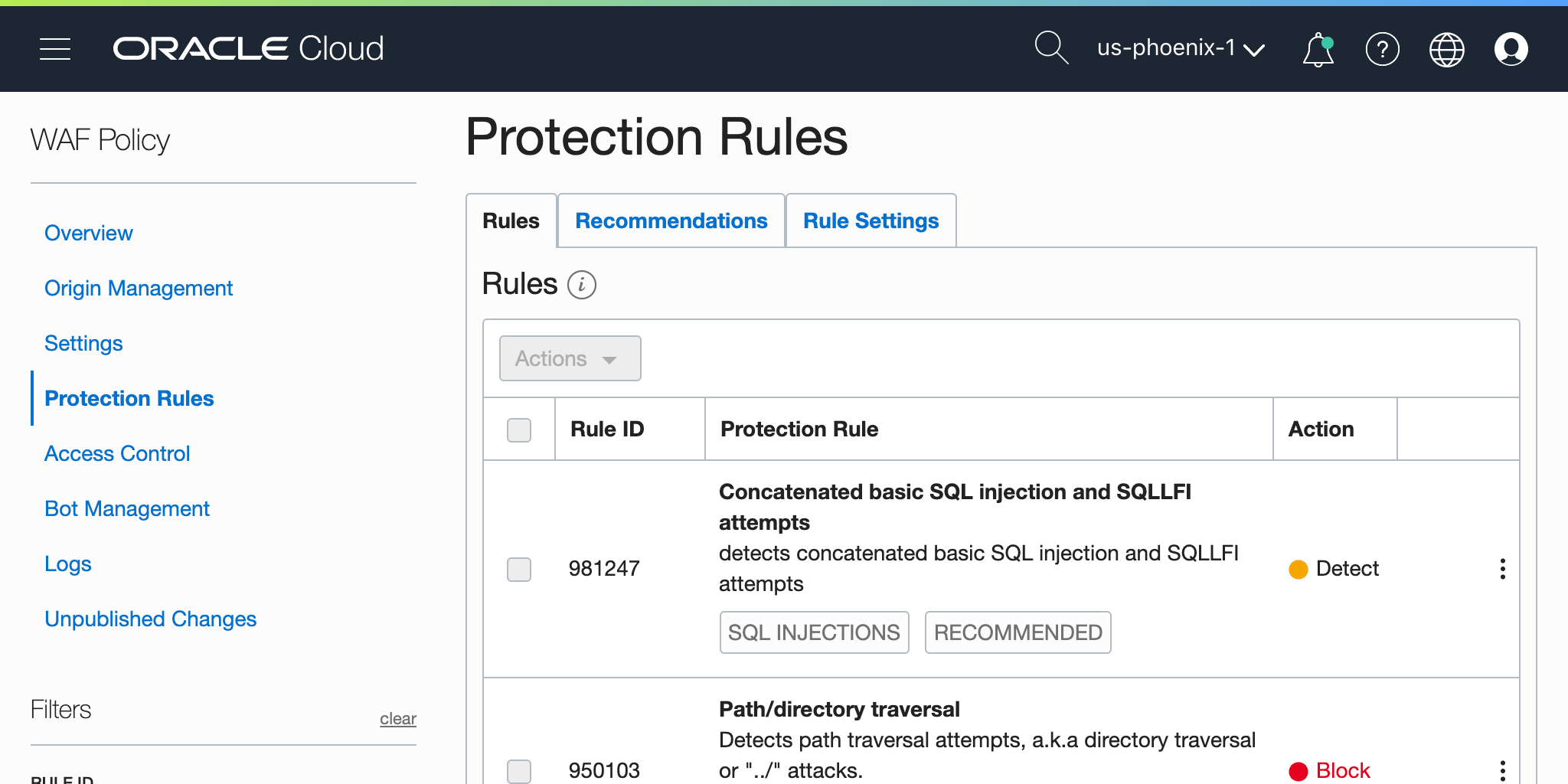
Applying protection to a WAF origin is done by choosing specific rules from OWASP Core Rule Set (CRS), where the action can be set to Detect, Block, or Off
WAF Access Rules
Custom access rules can also be defined based on a set of specified condition(s). Choosing the associative action, error code, and handling are defined as well
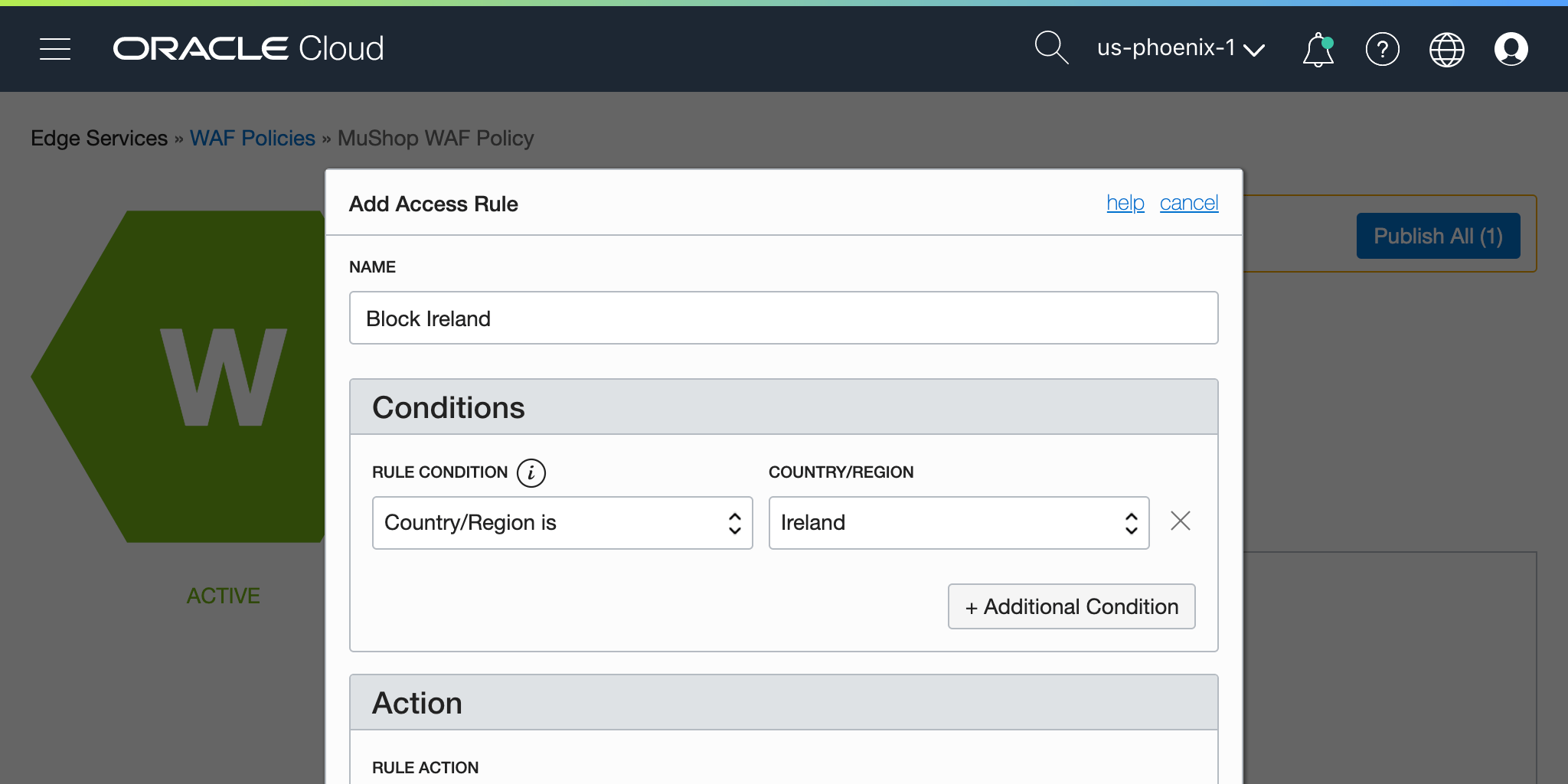
☝️ Here access from Ireland is blocked (sorry 🍀, demo purposes)
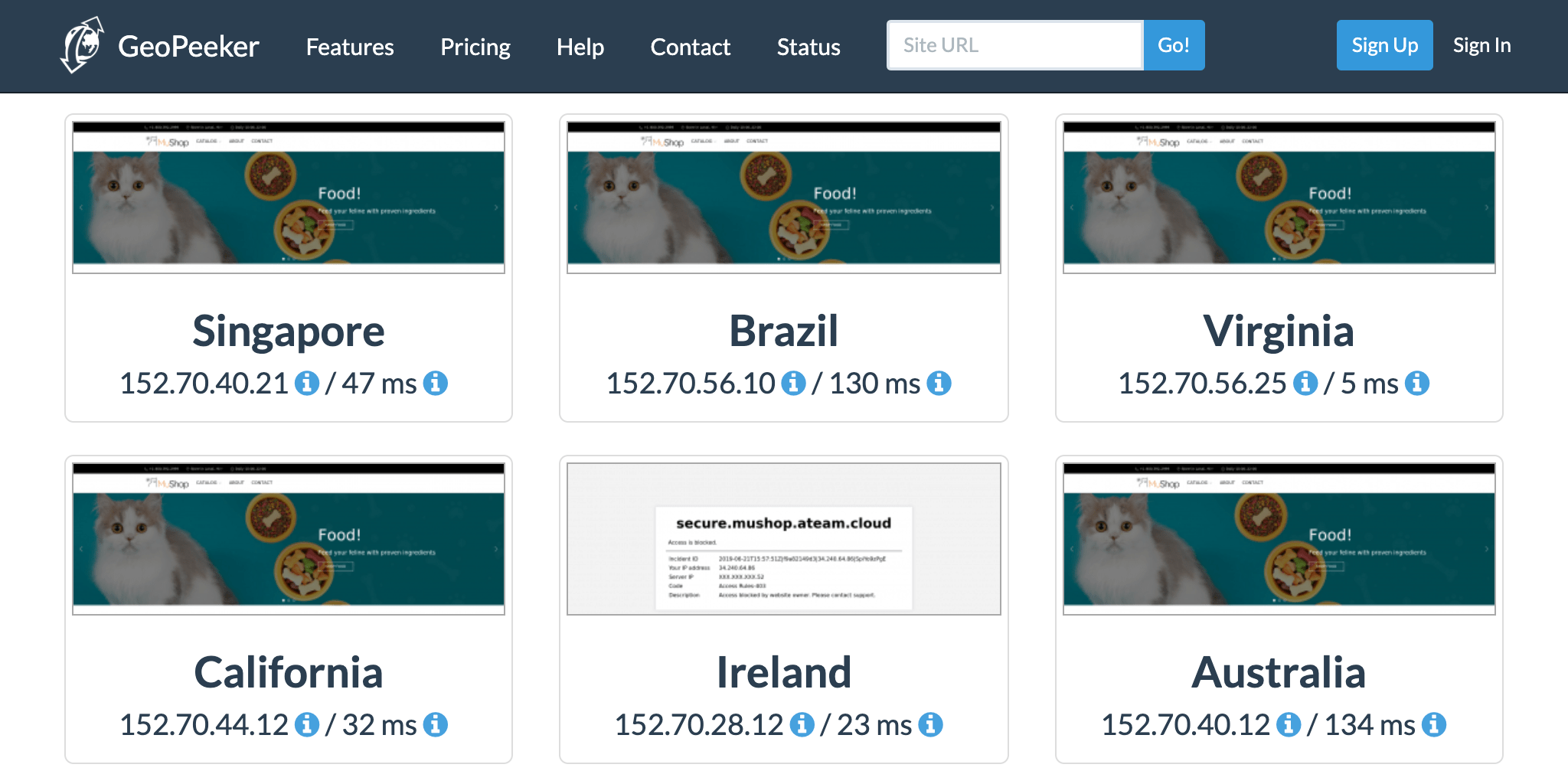
👿 Try It
WAF Demo
 DNS
DNS
 WAF
WAF

Verify WAF Edge
curl -I -X GET https://mushop.ateam.cloudcontent-type: text/html
vary: Accept-Encoding
x-cache-status: NOTCACHED
date: Sun, 23 Jun 2019 12:35:57 GMT
etag: W/"5d0b92c0-5fe5"
server: ZENEDGE
strict-transport-security: max-age=15724800; includeSubDomains
x-zen-fury: b9c90d1625d96f0414ad23c9562ea95ef6e80ed7
last-modified: Thu, 20 Jun 2019 14:05:52 GMT
x-cdn: Served-By-ZenedgeWe see server: ZENEDGE so WAF is working ✅
DEMO: OWASP Core Rule Set
For sake of demonstration, let's use the application search bar to attempt some attacks from the MuShop user interface. Try the following by entering text into the search field
⚠️ It may also be useful to open Chrome Developer Tools Network tab
;DROP TABLE users<script>alert('bad');</script>DEMO: WAF Access Control
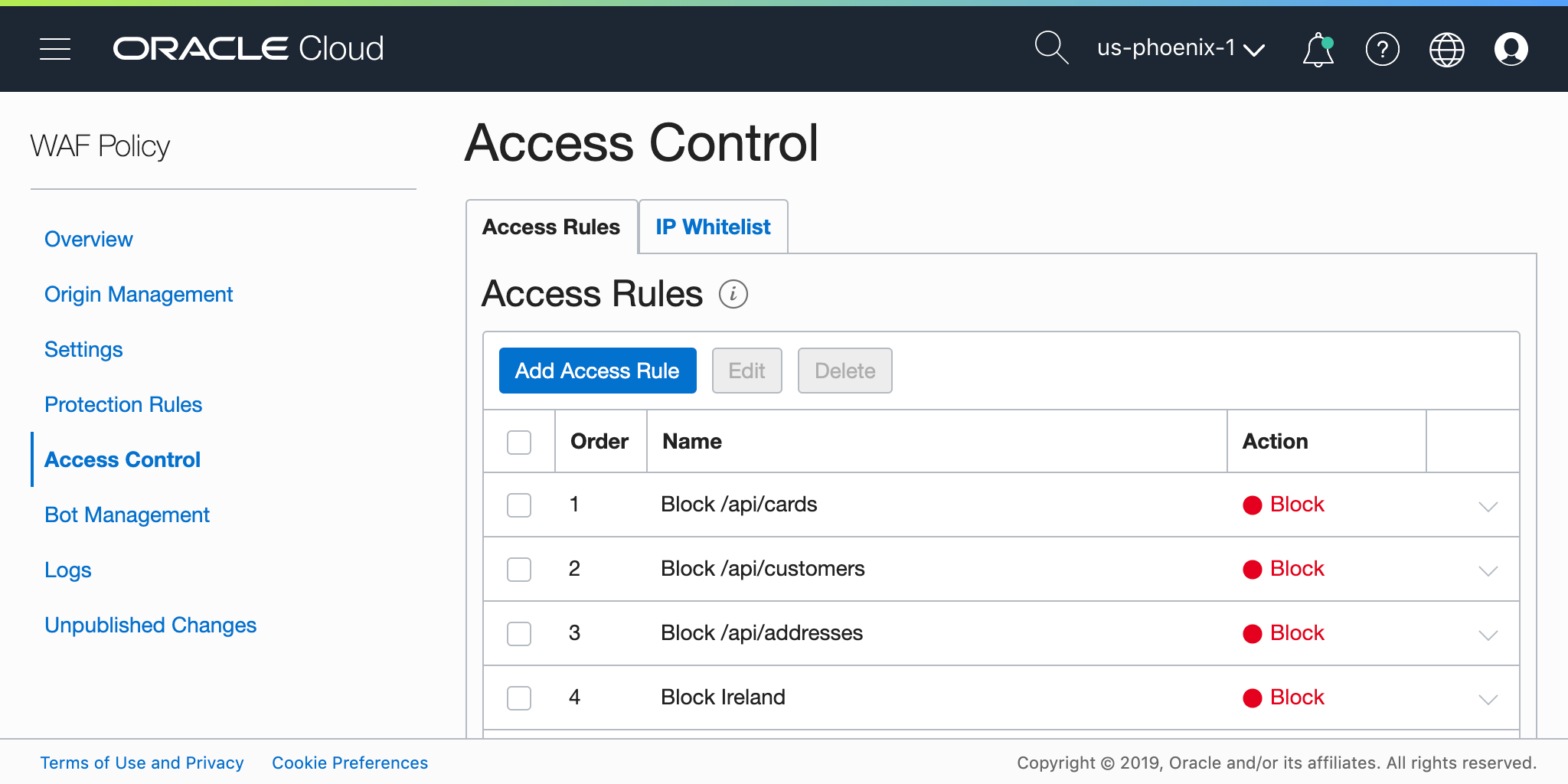
Other Edge Services
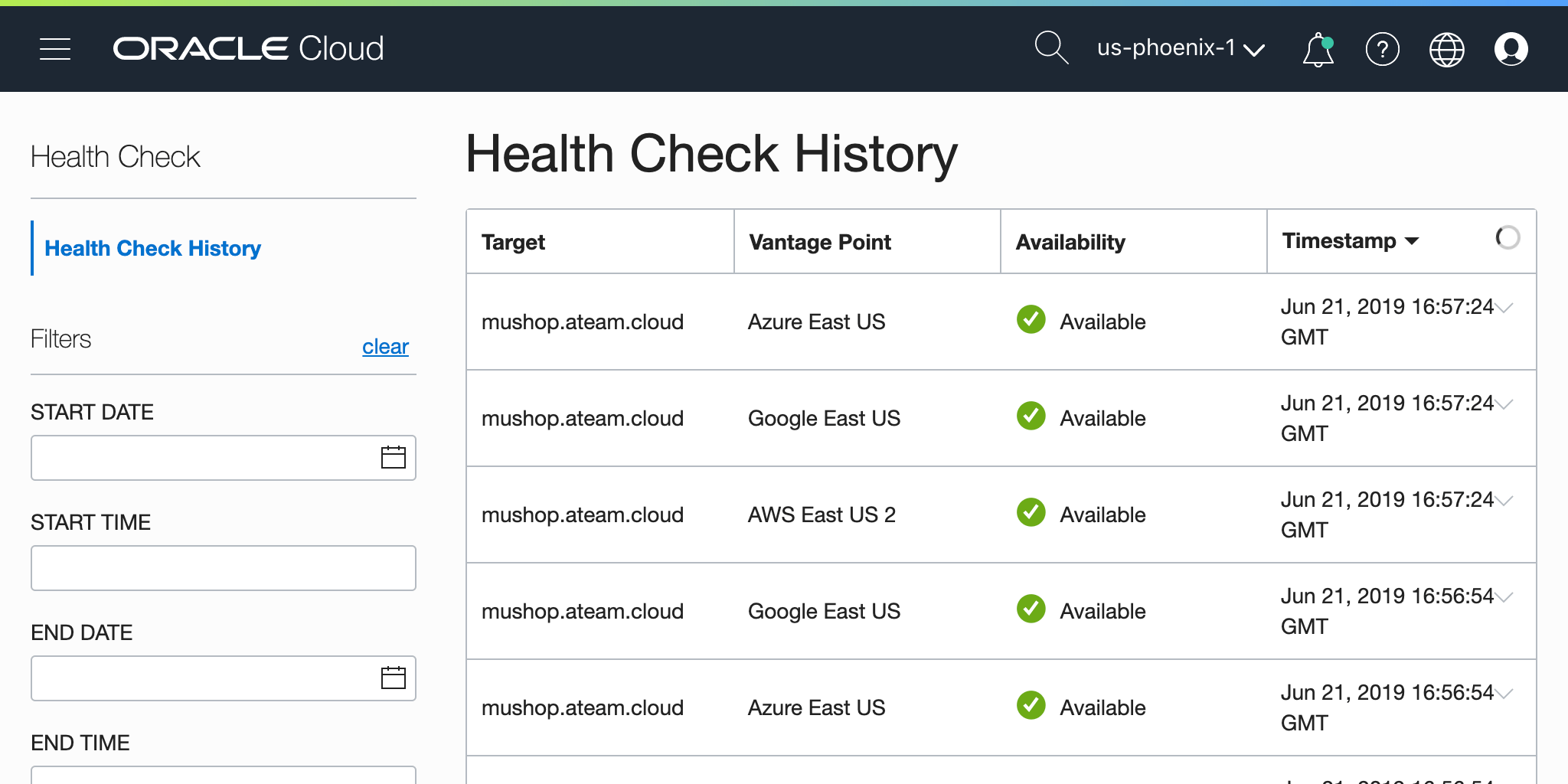
Health Checks
Provides users with high frequency external monitoring to determine the availability and performance of any publicly facing service, including hosted websites, API endpoints, or externally facing load balancers
Traffic Steering
Configure policies to serve intelligent responses to DNS queries, meaning different answers (endpoints) may be served for the query depending on the logic the customer defines in the policy.
☝️ Is directly connected to DNS and Health Check services!
